select the best answer. which of the following are breach prevention best practices
Two-factor authentication is a security feature that requires. All of this above.

The Three Elements Of Incident Response Plan Team And Tools
Misdirected communication containing PHI or PIIC.

. Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and. Which of the following are breach prevention best practices. What are best breach prevention practices.
Implementing encryption standards and backup policies to decrease risks and make sure that software is up. Select the best answer. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when.
Which of the following are breach prevention best practices. Which of the following are breach prevention best practices. Remediation Accessed N PHI transmitted orally PHI on paper PHI.
Top 4 Human Errors In Cyber Security How To Prevent. Identify areas that store transmit collect or process. Developing the IRP will help the IT staff of the company to control the data breach incidents.
Which of the following are breach prevention best practices Saturday June 11 2022 Edit. Employees have an important role in keeping their organizations secure. Access only the minimum amount of phipersonally identifiable information pii necessary.
Making weak passwords can be a reason for Data. And privacy officials select reasonable and appropriate. Best practices for breach prevent are.
Do you have strong password policy and is it being adhered to. Create Strong Policies Strong Passwords. 30 Best Practices for Preventing a Data Breach.
Best Practices for Preventing a Data BreachTrain Employees on Security Awareness. 12 charts show the. Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your.
Invest in the Right. All of the above A breach as defined by the DoD is broader than a HIPAA breach or breach defined by HHS. Which of the following are breach prevention best practices.
Promptly retrieve documents containing PHIPHI from the printer. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business. Identity sensitive data collected stored transmitted or processes.
Which of the following are breach prevention best practices. Promptly retrieve documents containing PHIPHI from the. Set up two-factor authentication for every account.
Which of the following are breach prevention best practices. Logoff or lock your workstation when it is unattended. Best practices for breach prevent are.
30 Best Practices for Preventing a Data Breach.

Top 6 Best Practices For Preventing A Data Breach

The Best Crisis Management Examples Smartsheet

8 Best Practices For Enterprise Email Security Fortinet

Onedrive Security Recommendations And Best Practices

How To Prevent A Data Breach 10 Best Practices And Tactics

Securitymetrics Guide To Hipaa Compliance
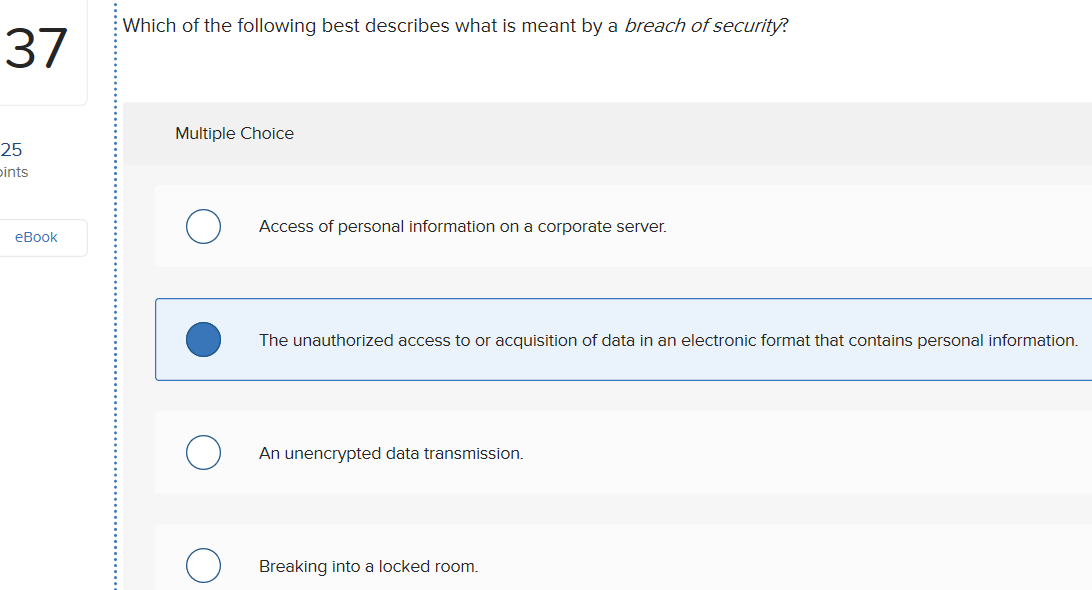
Solved Which Of The Following Best Describes What Is Meant Chegg Com

What Should A Company Do After A Data Breach Every Step To Take

Best Practices For Securing Sensitive Data In Aws Data Stores Aws Database Blog

Data Loss Prevention What Is Dlp How Does It Work
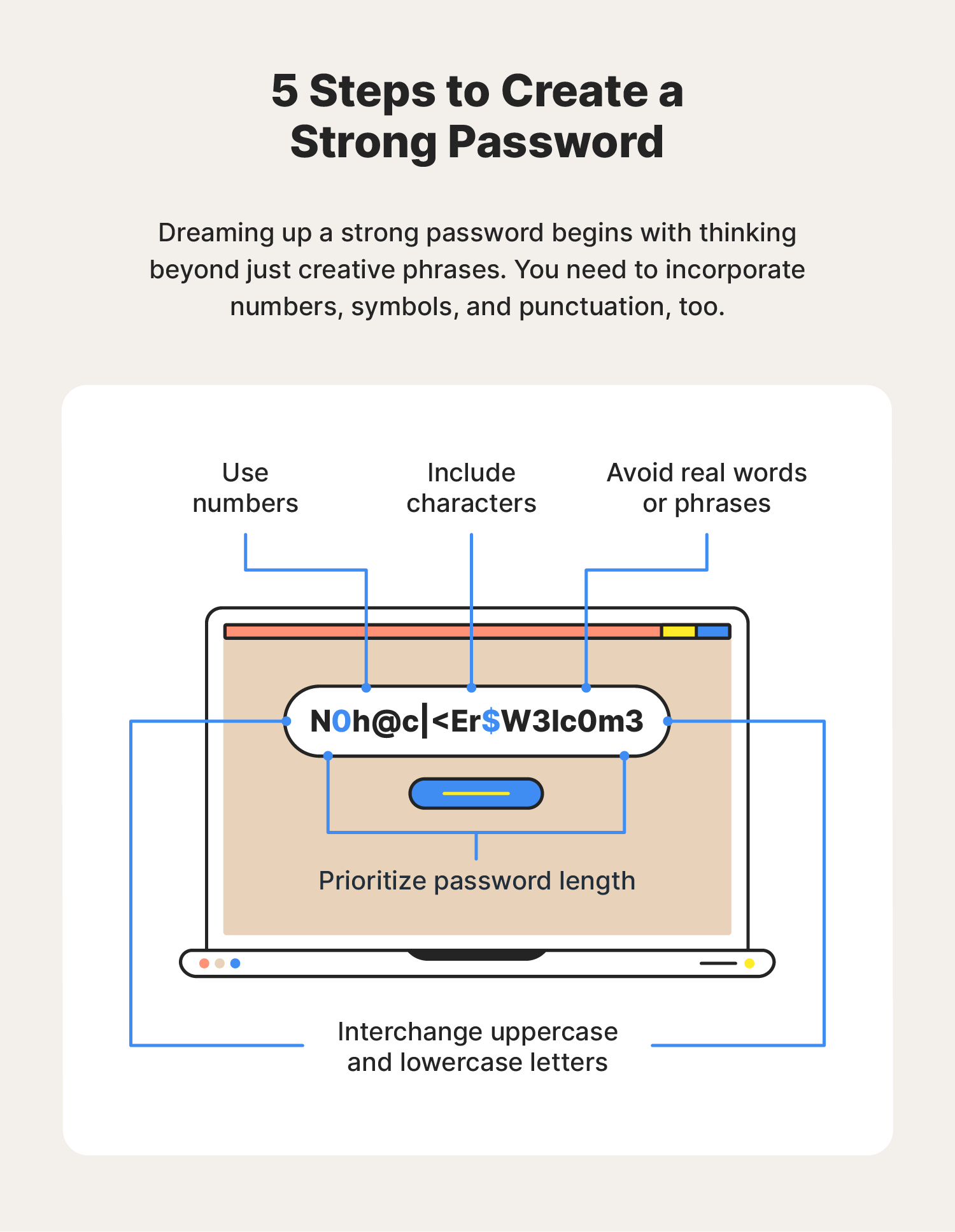
Password Security 10 Password Safety Tips Norton
What Is Zero Trust Implementation Best Practices And More Strongdm

Software Data Breach Overview Veracode
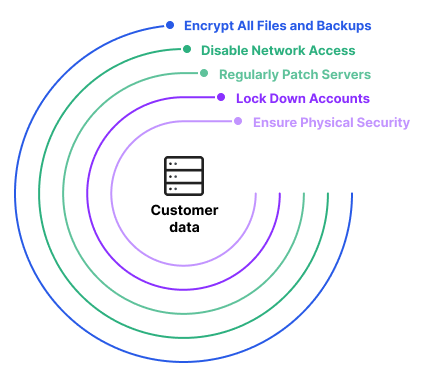
What Is Database Security Threats Best Practices Imperva
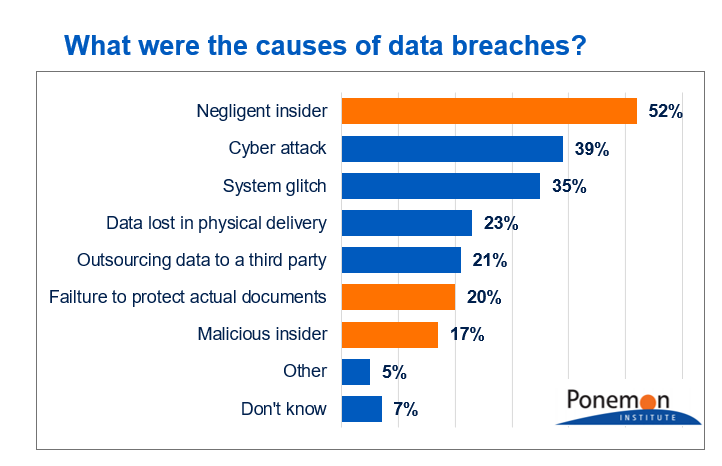
What Is Data Loss Prevention Acronis

Cybersecurity 101 Protect Your Privacy From Hackers Spies And The Government Zdnet
5 Best Practices For Keeping Amazon Aws S3 Buckets Secure

How To Prevent A Data Breach In Your Company

Comparing Crowdstrike Identity Protection Solutions Crowdstrike